
Your website is your business’s digital storefront. But what happens when that storefront is hijacked and replaced with offensive messages or strange images? That’s web defacement—and it’s not just a harmless prank.
Web defacement is a clear warning that your security systems have been breached. Beyond the visual damage, it can tarnish your brand’s credibility, scare off users, and open the door to deeper cyber threats. The good news? You can stop it before it happens.
What Is Web Defacement and Why Should You Take It Seriously
Imagine opening the official website of a government agency or a company, only to be greeted by bizarre images or provocative messages.
That’s web defacement, a form of cyberattack where hackers break in and modify the appearance or content of a website without the owner’s consent.
These attackers often insert malicious code that replaces text, images, and other visual elements. Their motives vary from pushing political or social agendas to simply showing off their hacking skills.
And the impact can be severe. For government bodies, businesses, or public service platforms, a defaced website doesn’t just look bad, it damages trust and credibility. Especially when the site plays a critical role in public communication or customer service, the consequences can ripple far beyond surface-level visuals.
How Do Web Defacement Attacks Happen?
Web defacement doesn’t just happen out of nowhere. Behind every attack, there’s a step-by-step process that hackers follow to take over a website’s appearance. Here’s a general breakdown of how it works:
Finding Security Gaps
Hackers begin by scanning for vulnerabilities, whether it’s flaws in the website’s code, weaknesses in the hosting server, or misconfigurations in the database. Common methods like SQL injection, brute force attacks, and cross-site scripting (XSS) are often used to gain access to the backend.
Injecting Malicious Code
Once inside, attackers plant malicious scripts, HTML, CSS, or JavaScript, that replace the original website content with fake messages, offensive visuals, or even hidden malware targeting unsuspecting visitors.
Keeping the Door Open
To maintain long-term access, attackers often install a backdoor. This could involve phishing for admin credentials or reusing previously stolen login data. In many cases, site owners don’t even realize their system has been compromised, until it’s too late.
Real-World Examples of Web Defacement and the Impact

Web defacement is more than just a digital prank. In many cases, it signals a serious breach in a website’s security, and the consequences can be severe, ranging from data leaks to reputational damage.
Generally, defacement attacks fall into two categories.
- Basic Defacement
This is the most common type. Hackers simply replace the website’s visuals and add a message, often to announce the site has been hacked or to expose its weak security.
- Advanced Defacement
Far more dangerous, this type goes beyond appearance. It often includes data theft, malware injection, and redirecting traffic to malicious sites, posing real risks not just to the site owner but also to its visitors.
3 Notable Cases of Web Defacement
NHS UK (2018)
A patient survey website operated by the UK’s National Health Service (NHS) was hacked, displaying the message “Hacked by AnoaGhost.” Although the defacement was removed within hours, it was later revealed that the breach had lasted for nearly five days. The incident sparked major concerns over the security of citizens’ medical data.
Google.ro & PayPal.ro (2012)
In Romania, users trying to access the local versions of Google and PayPal were redirected to a defaced page. This attack used DNS hijacking and was carried out by an Algerian hacking group known as MCA-DRB, responsible for over 5,000 defacement incidents worldwide.
Georgia (2019)
The country of Georgia experienced one of the largest cyberattacks in its history. More than 15,000 websites, including government portals, local media, banks, and TV stations, were defaced or taken offline. The attack was linked to a breach of the local web hosting provider’s infrastructure, exposing widespread systemic vulnerabilities.
3 Effective Ways to Prevent Web Defacement
When it comes to web defacement, prevention is far more effective than damage control. By combining the right technical strategies with strong security policies, you can significantly reduce the risk of such attacks.
Here are three proven methods to safeguard your website.
1. Security Audits & Penetration Testing
The first step is identifying your system’s weak points. Regular security audits and penetration testing help uncover potential vulnerabilities, giving you the chance to fix them before hackers do.
2. Real-Time Monitoring
Deploy real-time monitoring tools that detect any unauthorized changes to your website. If suspicious modifications are spotted, the system can instantly alert your IT team, allowing them to act quickly and contain the damage.
3. Routine Data Backups
Attacks can happen when you least expect them. With regularly scheduled backups, you can restore your website’s content and appearance quickly, minimizing downtime and preserving user trust.
Stop Web Defacement Before It Starts: Meet F5 Web App Scanning
Web defacement can happen anytime, and unfortunately, many only realize it after their website has already been compromised. But there’s a better way: act before hacker strike. One of the most proactive solutions you can deploy is F5 Distributed Cloud Web App Scanning.
More than just a scanning tool, F5 is a cloud-based service that automatically scans your web applications and APIs, identifies hidden security flaws, and even simulates real-world attacks before the bad actors get a chance.
With F5, you don’t just discover the problem, you also get actionable insights on how to fix it.
How F5 Distributed Cloud Web App Scanning Works: Automated, Proactive, and Thorough 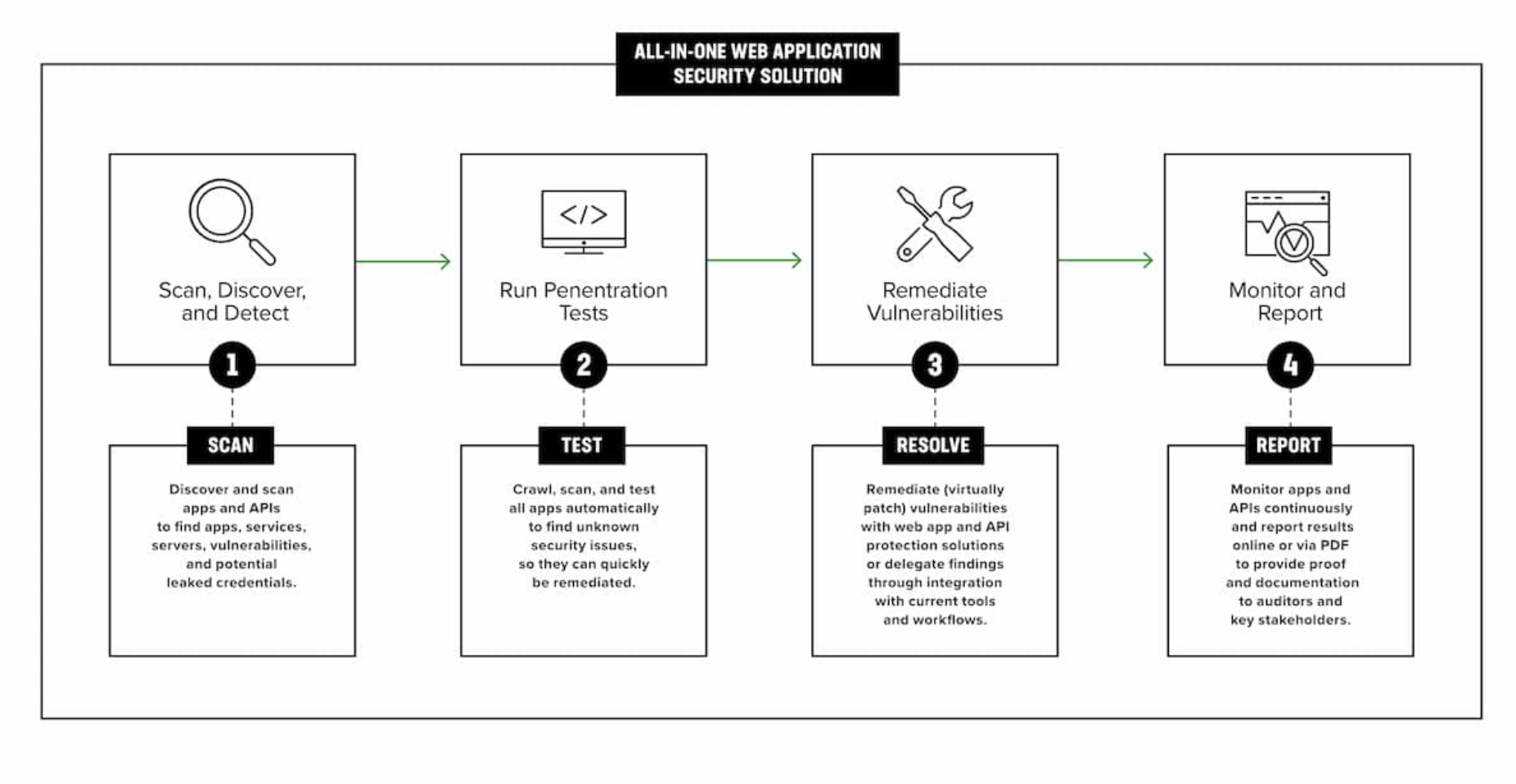 Source: F5 Distributed Cloud Web App Scanning
Source: F5 Distributed Cloud Web App Scanning
F5 doesn’t just alert you to vulnerabilities, it helps you close them before they’re exploited. Here’s how it works:
- Mapping Your Digital Assets
F5 begins by mapping all public-facing assets, including subdomains, endpoints, and APIs. This is crucial, as vulnerabilities often hide in overlooked corners of your infrastructure.
- Identifying Technologies & Vulnerabilities
The system automatically detects the technologies your website uses (frameworks, CMS, libraries) and cross-references them with known vulnerabilities like those listed in the OWASP Top 10.
- Automated Attack Simulations
F5 simulates real-world attacks, including SQL injection, XSS, and AI-based exploits, helping you find and patch weak points before hackers do.
- Detailed Reports & Guided Remediation
You’ll receive a clear, visual report complete with screenshots, exploit simulation videos, and step-by-step mitigation recommendations.
Key Features & Benefits of F5 Web App Scanning
- Early Detection, Fast Action: Catch potential threats before they escalate into major incidents.
- Built for Modern Applications: Optimized to protect API-heavy and AI-powered applications, prime targets in today’s threat landscape.
- DevOps-Friendly Integration: Easily integrates into your CI/CD pipeline, making security part of your development process, not a roadblock.
- Automated Monitoring & Real-Time Alerts: F5 watches for anomalies 24/7 and alerts your team instantly so you can act before damage is done.
Secure Your Website Now with CDT!
Don’t wait until your site is defaced to take action. Start protecting it today with F5 Distributed Cloud Web App Scanning, your front-line defense against hidden vulnerabilities and malicious threats.
Central Data Technology (CDT), a member of CTI Group and the authorized distributor of F5 in Indonesia, is ready to help you secure your websites and APIs through automated and comprehensive protection.
Consult your security needs today through the link below and safeguard your digital infrastructure with confidence.
Author: Wilsa Azmalia Putri – Content Writer CTI Group

